ENIGMA In 1925 the German Army purchased several examples of a commercially produced cipher machine called the ENIGMA, manufactured first by Chiffriermaschinen Aktiengesellschaft, a company owned by Arthur Scherbius, and later by Chiffriermaschinen Gesellschaft Heimsoeth und Rinke After some modification, the ArmyAtion of the commercial cipher pachine It was called Funkschlussel C (literally meaning "radio key") By 1928, the German army introduced its own 6 by Gary M Bat eman 2 version as well Enigma G Both Enigma C and Enigma G used three changeable cipher rotors which offered too few permutations in their daily key settings and were consideredA capsule account of how the Poles and British broke the Army Enigma "The German cipher machine Enigma", Matematik Sider, September 14

Enigma Code Breaking Machine Rebuilt At Cambridge
How to decode enigma code
How to decode enigma code-A cipher, on the other hand, makes a word or phrase secret by changing or rearranging the individual letters in a message Together, codes and ciphers are called encryption ENIGMA was a cipher machine—each keystroke replaced a character in the message with another character determined by the machine's rotor settings and wiring arrangementsThis version of cryptii is no longer under active development Find the latest version on cryptiicom Cryptii is an OpenSource web application under the MIT license where you can encode and decode between different format




Rare World War Ii Enigma Machine Sold For 45 000 Euros
The Enigma Code was invented by Arthur Scherbius in 1918, and took the world by storm due to its use in World War 2 The Germans used a very complicated machine called an Engima Machine in order to encrypt their messages During the 19s and 1930s, Germany developed a portable, easytooperate cipher machine known by its brand name Enigma All three branches of Hitler's armed services utilized it I don't understand why you have 5 identical copies of the same function In the Enigma Machine the rotors had different permutations wired up inside them Besides that, you should be able to have one copy of the code and logic,
Enigma Up close with a Nazi cipher machine It wasn't a computer, but it created encryption so advanced that humans needed machines to crack the codeThe main focus of Turing's work at Bletchley was in cracking the 'Enigma' code The Enigma was a type of enciphering machine used by the German armed forces to send messages securelyCaesar cipher is also known as Shift Cipher This shifting property can be hidden in the name of Caesar variants, eg CD code, C = D, the shift is 1 Jail (JL) code, J = L, the shift is 2 Ellen (LN) code, L = N, the shift is 2 Cutie (QT) code, Q = T, the shift is 3 Eiffel (FL) code, F = L, the shift is 6 WC code, W = C, the shift is 6
The Technology and History of the Enigma Cipher Machine 7 Enigma Technology Typewriter style cipher machine was a major advance in ease of use and cryptologic strength Innovation was the electro mechanical rotors to encipher / decipher messages Pressing a key causes the rotors to turn, giving a new cipher algorithm for Fascinating fact One of the earliest German cipher machines was named Enigma after Elgar's Variations Hence the UK's efforts to crack the "Enigma Code" in The Enigma Code The Enigma code, a very sophisticated cipher, was used during the Second World War by the Germans It involved an Enigma machine, similar to a typewriter, where pressing a letter would make the cipher letter light up on a screen




Decoding The Project Languages Code And Ciphers Richard Gallon We Are Here




Enigma The German Cipher Machine Enigma Machine Enigma Alan Turing
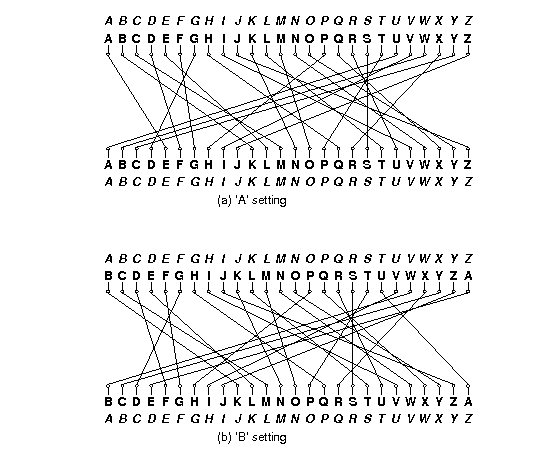
Codes and Ciphers This is a supplementary page illustrating Tony Sale's sequence of pages on the Enigma A detailed working through of Enigma encipherment The Enigma machine gives a mechanised way of performing one alphabetic substitution cipher after another An Enigma Machine uses a very complicated set of encryption criteria, and without knowledge of what settings were used for encryption, it is virtually impossible to decrypt (Access to large amounts of encrypted messages and some known plaintext was the only way the British ever managed to crack any Enigma messages) A FULLY OPERATIONAL ENIGMAI THREEROTOR CIPHER MACHINE ESTIMATE $1,000–180,000 (OFFERED AT NO RESERVE) The design of the Enigma was ingenious Each EnigmaI machine came with a set of 5 interchangeable electromechanical cipher wheels, known as rotors The rotors had 26 contacts on one side, and 26 pins on the other




Paper Enigma Machine Youtube
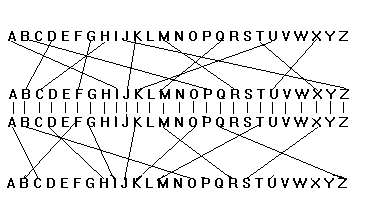



The Enigma 1
Turing and the team at Bletchley was not the first to break the Enigma code; "The Enigma Code Breach" by Jan Bury "Enigma" and Intelligence "The Enigma machine and Bletchley Park", Cybertwists "wwwenigmahistoryorg" Archived from the original on ; A character CAN map to itself so a big flaw in original Enigma is solved So the keyspace would be formed from selecting 10 rotors in random from 47, and setting an initial start position of each into any of the 47 possible positions So Keyspace would be 47^ = 2773 or roughly 111 bits




Enigma I A Fully Operational Three Rotor Enigma I Cipher Machine Berlin Heimsoeth Und Rinke 1943 History Of Science And Technology Including Fossils Minerals And Meteorites Books Manuscripts Sotheby S



The Enigma Machine And The Ultra Secret South African Military History Society
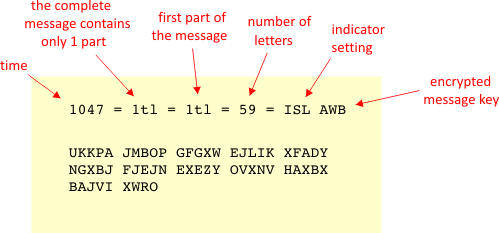
The number "65" represents the number of letters in the actual message, so the Radio Operator and Enigma Decoder can confirm they have the entire message The "=" are just place holders, much like a STOP in a Telegram or, in the case of Enigma, an "X" You'll find these throughout the body of the message FEW GHT =CryptiiText to Enigma Cryptiiv2 Cryptii Convert, encode, encrypt, decode and decrypt your content online Attention!Browse 236 enigma code stock photos and images available, or search for alan turing or bletchley park to find more great stock photos and pictures Working Enigma cipher machine that along with the 1942 56page notebook belonging to codebreaker Alan
.jpg?mode=max)



World War Ii Enigma Machine A Three Rotor Enigma Cipher Machine Ca 1939 Number A 441




Enigma Machine Emulator 101 Computing
Cracking Enigma is considered one of the major factors in the outcome of WW2 and remains one of the most important historical cases relating to cryptography and codebreaking today CNET Beto O The Germans began using the Enigma machine in the late 19s By late 1932, the Poles had broken the Enigma code In 1939 just a matter of weeks before Hitler invaded Poland, the Polish Cipher Bureau shared its technology with the French and the British, who continued to decode messagesEnigma cipher tool This is a tool to encrypt or decrypt messages using an Enigma cipher machine simulator If you do not know the correct settings for decryption, it can also be used to try out a large number of settings and look for plaintext messages that look similar to text written in a selected language, ie crack the code




Operation Turing



Enigma Procedure
That had been done years before by the Polish Cipher Bureau And the imposing machine that is a central feature of the movie and which is supposed to have broken the key German naval code was not designed by Turing nor was it built at BletchleyProbably a polyalphabetic cipher This means that every letter of the plain text is replaced by a single corresponding letter in the cipher text The cipher letter depends on the position of the plain letter in the plain text A similar cipher was produced by a commercial machine Enigma that had been on sale since 1926 So the PolishThe Polish Cipher Bureau initiated the French and British into its Enigmabreaking techniques and technology at a conference held in Warsaw From this beginning, the British Government Code and Cypher School at Bletchley Park built up an extensive cryptanalytic facility Initially, the decryption was mainly of Luftwaffe and a few Army messages,
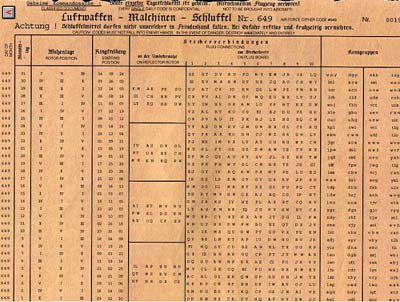



Exploring The Enigma Plus Maths Org




How To Make Your Own Papercraft Enigma Code Machine The Mary Sue
Enigma I electromechanical cipher machine, 1935, featuring an ebonite Steckerbrett (plugboard) on the front, which was exclusive to the German armed forces and exponentially increased the complexity of the code This version of the Enigma is sometimes referred to as the Heeres (Army) Enigma, Wehrmacht Enigma, or Luftwaffe Enigma due to its Like all the best cryptography, the Enigma machine is simple to describe, but infuriating to break Straddling the border between mechanical and electrical, Enigma looked from the outside like anThe Enigma cipher was eventually broken by Alan Turing and a group of scientists at a later date during the war The breaking of this code led to the Allies' ability to intercept and decode the Germans' messages, which had wonderous effects on the outcome of the war




Ultra Allied Intelligence Project Britannica




Pin On Science
This is the code that will apply the Caesar cipher function encrypt (char) The Caesar cipher is probably one of the most basic ciphers, although it was the basis of the Enigma code The enigma machine was used in World War II to encrypt secret messagesThe Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines becameThe flaw which allowed the Allies to break the Nazi Enigma codeMore links & stuff in full description below ↓↓↓First video explaining Enigma http//youtub




The Enigma Cipher Machine And Breaking The Enigma Code
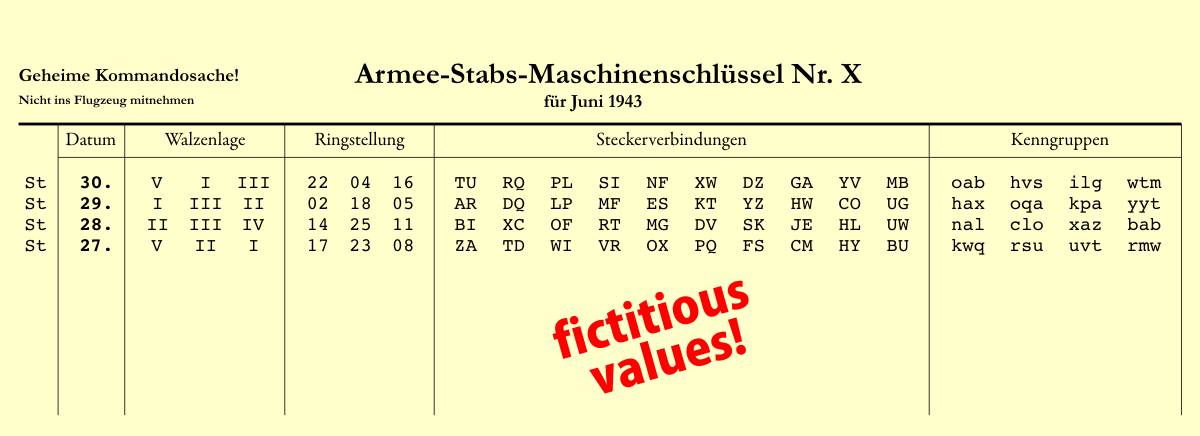



Enigma The German Cipher Machine
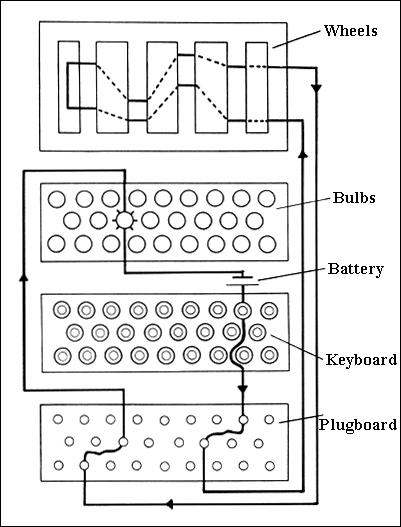
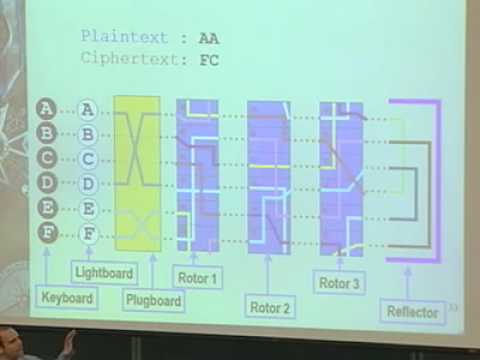
An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakableThe Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Bitwise calculator Text to base64 Bootstring converter Nihilist cipherEnigma machine The Enigma machines were used during World War II by the Germans to protect their communications It came in different models, but they all built on the same principles It had a keyboard, rotors, a plugboard, a reflector and a lampboard to show the results The Enigma machine encryption was broken during World War II by




The Enigma Encryption Machine Video Khan Academy
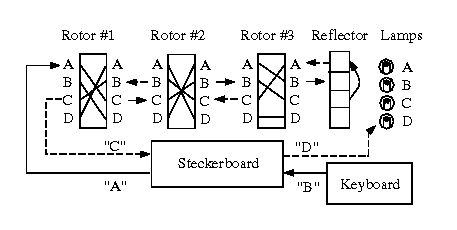



Cryptology I Vigenere Based Systems
Introduction, Binary Numbers, Error Detection, Secret Codes, The Enigma, Public Key CryptographyThe U570 may have yielded not only its Enigma machine to the British, but also its valuable code books and ciphers Imperial War Museum photo The use of secret messages to communicate sensitive information is as old as the art of war itselfEnigma Cipher Machines This page is about the famous Enigma cipher machine, well known for the vital role it played during WWII Below are descriptions of the various models, their manufacturers, some accessories, patents, computer simulations and codebreaking There is no such thing as the Enigma In fact, Enigma is the brand name of a series of cipher machines,



Fhcam Enigma Machine




Enigma Machine Wikipedia
As technology increases, so do the methods of encryption and decryption we have at our disposal World War II saw wide use of various codes from substitutionEnigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that Getty Images In World War II, the Allies faced a dilemma The German Enigma machine created encrypted messages, and the Germans changed the code every day Even if a code



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
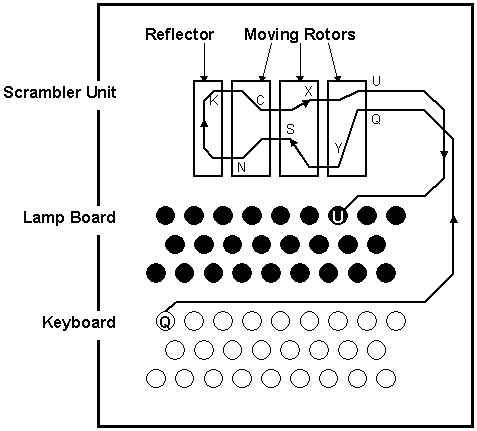



Enigma And A Way To Its Decryption
CodeBreaking, Cipher and Logic Puzzles solving tools (or cypher) is a method for protecting data through encryption and decryption Most ciphers require a specific key for encryption and decryption, but some ciphers like the ROT13 or Atbash ciphers have fixed keys Enigma machine Foursquare cipher Gronsfeld cipher Keyed caesar cipher




Build Your Own Enigma Cipher Machine Ieee Spectrum
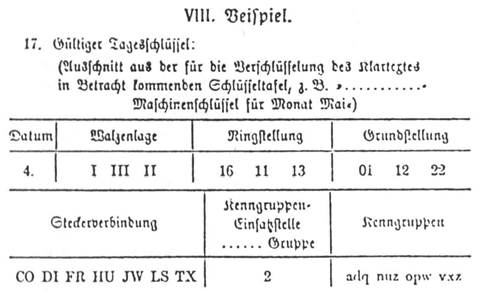



Enigma Codeproject



Enigma Procedure




How To Crack The Enigma Cipher Youtube
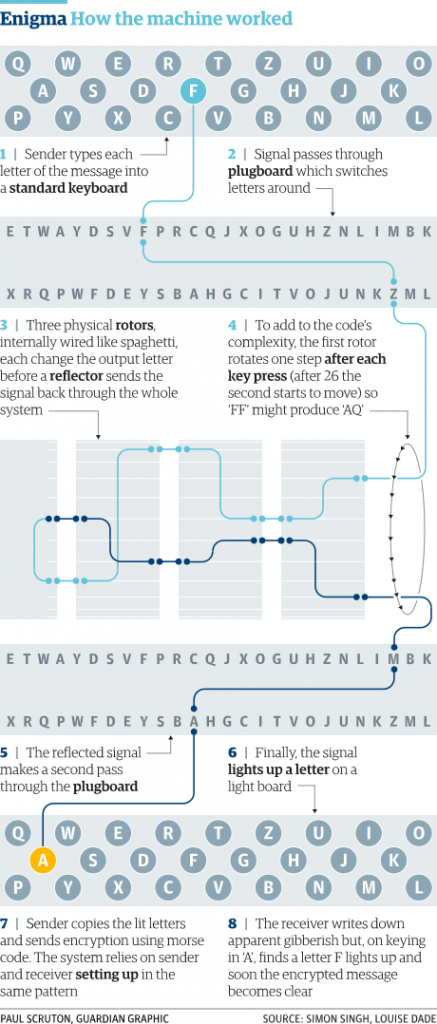



The Imitation Game How Did The Enigma Machine Work Science Abc




Enigma Definition Machine History Alan Turing Facts Britannica




Enigma Technology And The History Of Computers



Cryptography How Much Time It Would Take To Decode Enigma Code Machine If Modern Computers Were Available Quora



1



3



1




Cipher Machines
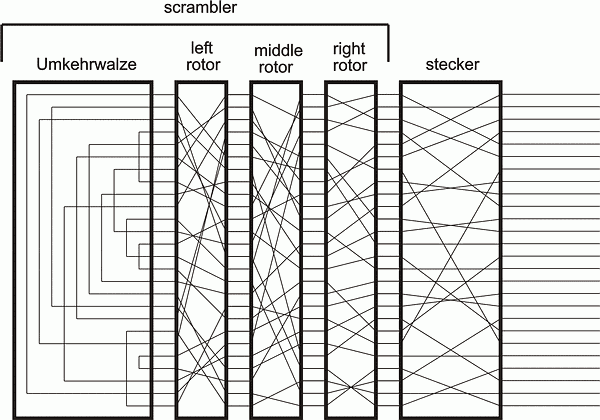



The Encryption War Of Wwii The Enigma Encryption Machine Engineering And Technology History Wiki




Capture Of U 570 And Its Enigma Cipher Machine Argunners Magazine



Enigma Cipher




Enigma Machine High Resolution Stock Photography And Images Alamy




Enigma Code Breaking Machine Rebuilt At Cambridge




The Inner Workings Of An Enigma Machine Youtube



Enigma The German Cipher Machine
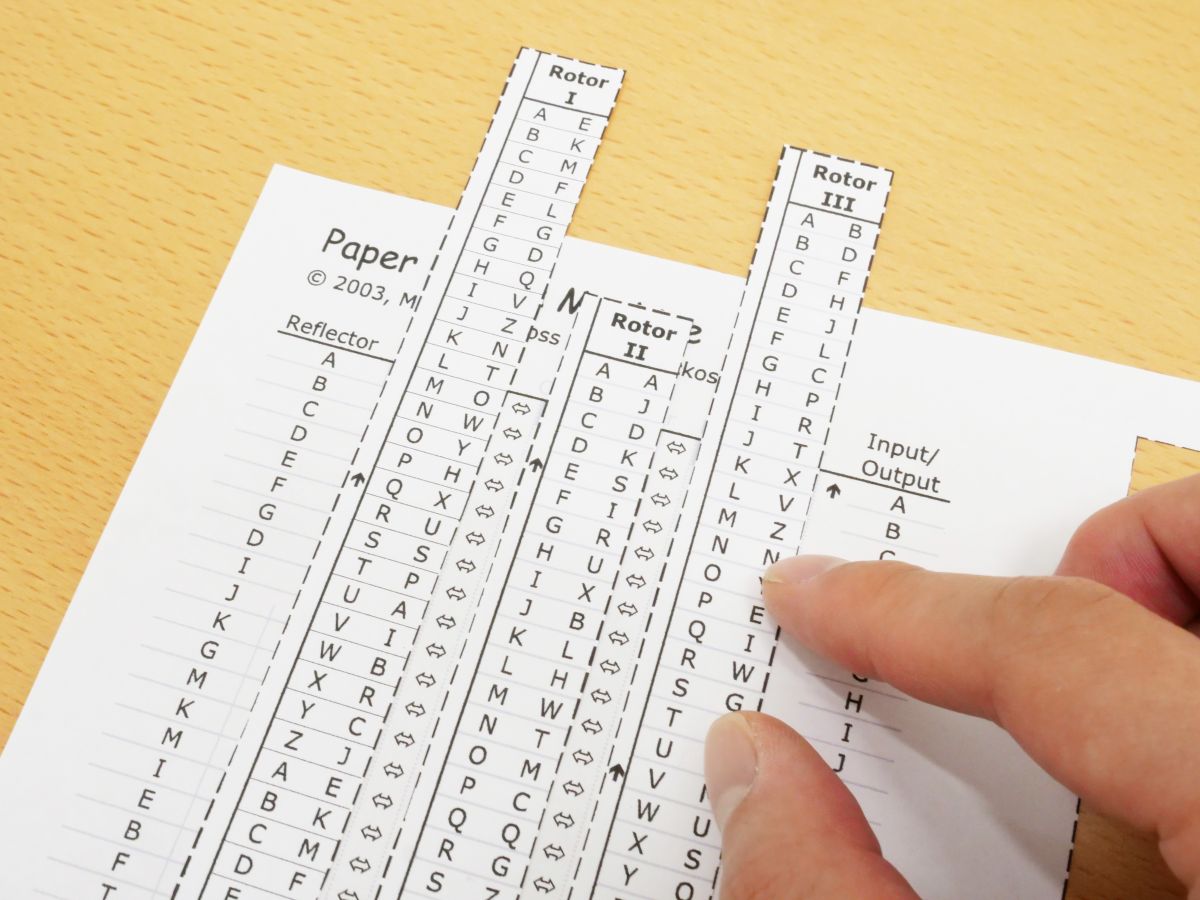



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




Cxncjoa77wzf6m




Original Relic Part From Enigma Cipher Code Machine



Http Www Cimt Org Uk Resources Codes Codes U Text Pdf




Bletchley Park Enigma



Naval Enigma



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Lab 4 Enigma The Purpose Of This Lab Is To Practice Good Oop Practices You Will Write A Program That Encrypts And Decrypts Messages Simulating A Simplified Version Of The Enigma Machine Used By The Germans In Wwii The Machine Will Be Described In




Nazi Enigma Code Machine Like In Imitation Game Goes To Auction Bloomberg




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond



A Riddle Called Enigma




Zygalski Sheets Wikipedia




Rare World War Ii Enigma Machine Sold For 45 000 Euros



Enigma Machine




Rare Nazi Enigma Code Machine Tops 143 000 At Auction Europe News Top Stories The Straits Times




How Alan Turing Cracked The Enigma Code Imperial War Museums




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium




Breaking The Code The Secrets Of Enigma Cipher Machines Books Manuscripts Sotheby S
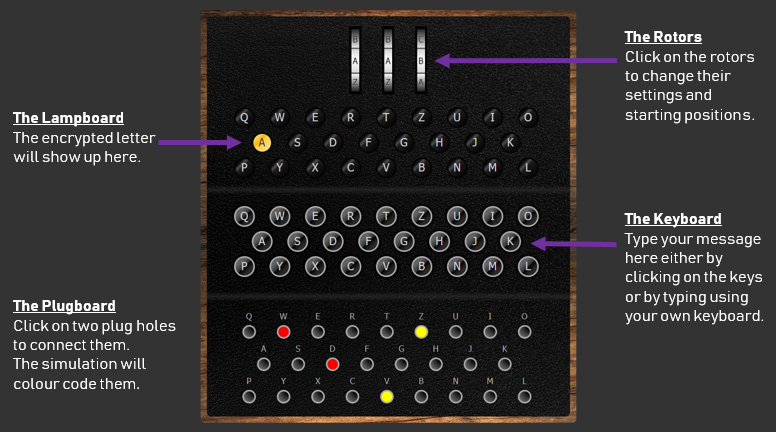



Enigma Encoder 101 Computing




Reflector Cipher Machine Wikipedia




Enigma Machine Wikipedia



Enigma Machine
/https://public-media.si-cdn.com/filer/f5/95/f59548db-c8c7-47a0-8404-9e44cd4b8db6/enigma.jpg)



Wwii Enigma Machine Found At Flea Market Sells For 51 000 Smart News Smithsonian Magazine



The Polish Attack On Enimga




Digitalocean Blog



What Alan Turing Can Teach Us About Product Management Chargebee S Saas Dispatch




How The Enigma Works Nova Pbs



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



Project 1 Cs 61b Fall 19




Breaking Enigma A Story Of European Co Operation Science Museum Blog




Enigma Machine Wikipedia




Enigma Machine Wikipedia




Allies Capture German Enigma Machine May 9 1941 Edn



Enigma Paper Enigma Franklin Heath Ltd Wiki




Cipher Machines From Antiquity To The Enigma Machine




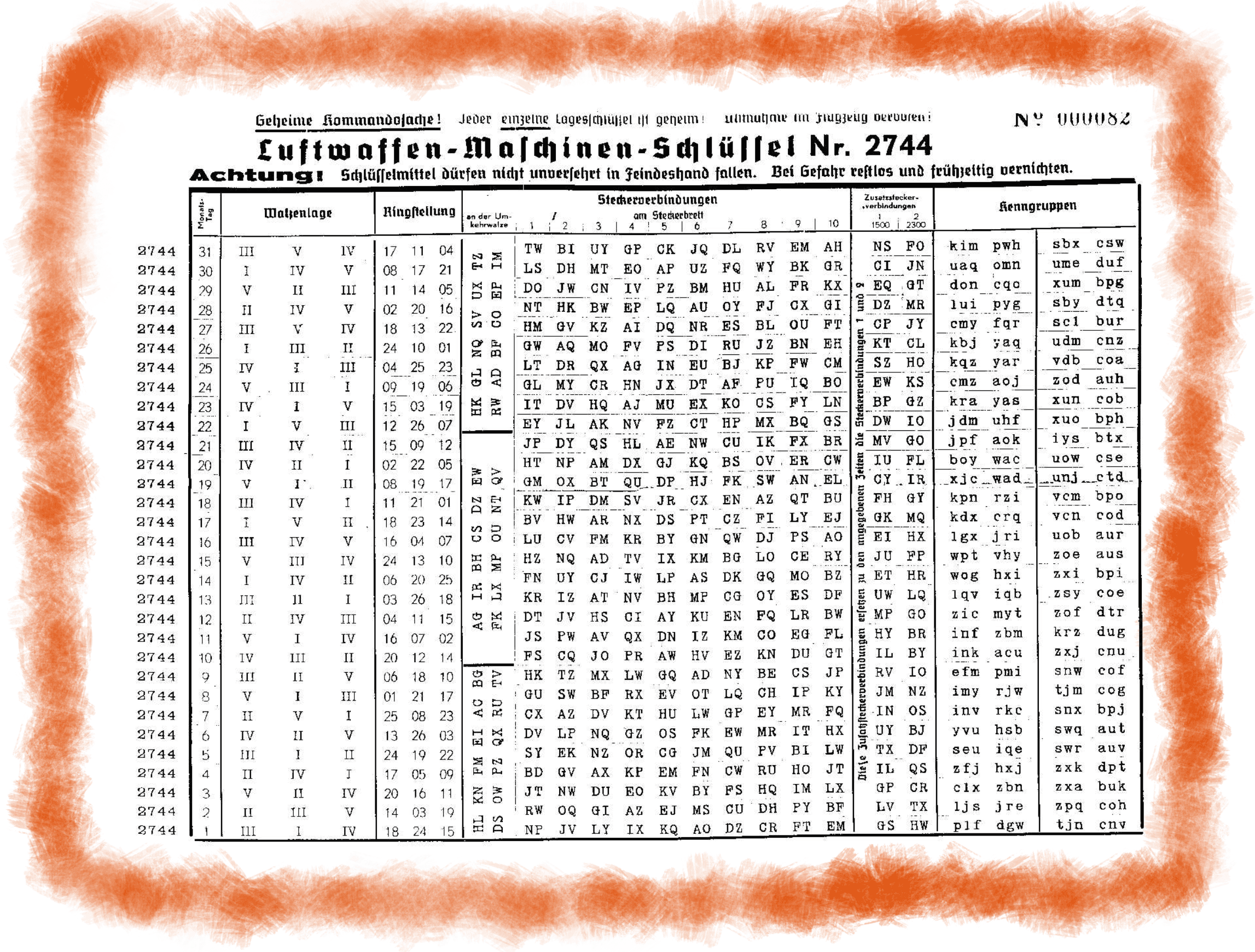
Enigma Daily Settings Generator 101 Computing



3




Home Make Diy Projects And Ideas For Makers Enigma Machine Ciphers And Codes Enigma




World War Ii Enigma Machines Antique Trader



The Enigma Code Youtube




Bletchley Park Enigma




The Enigma Enigma How The Enigma Machine Worked Hackaday
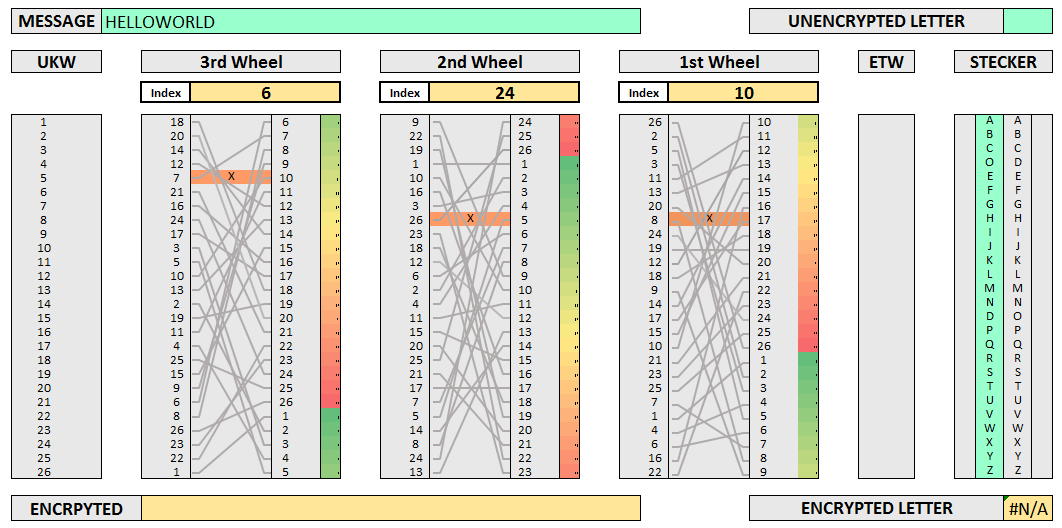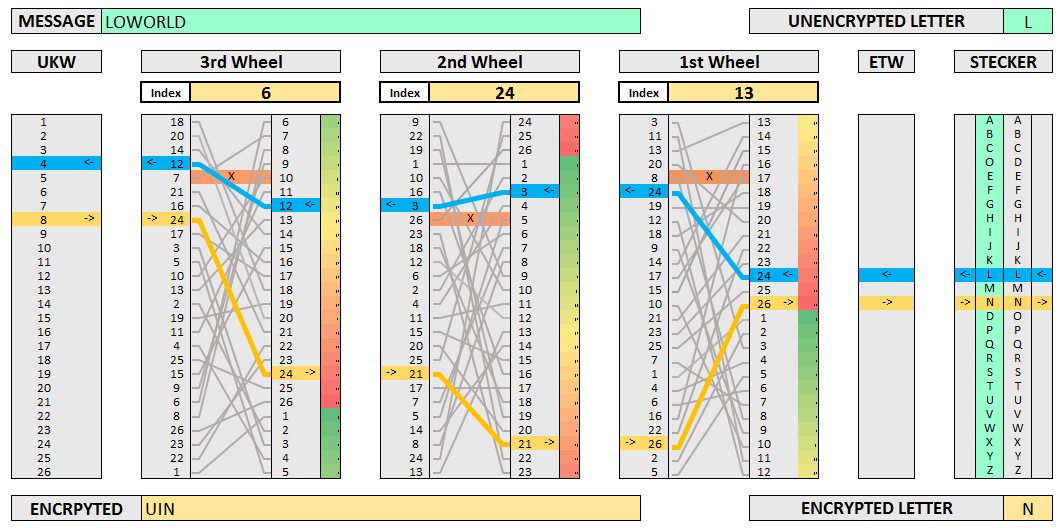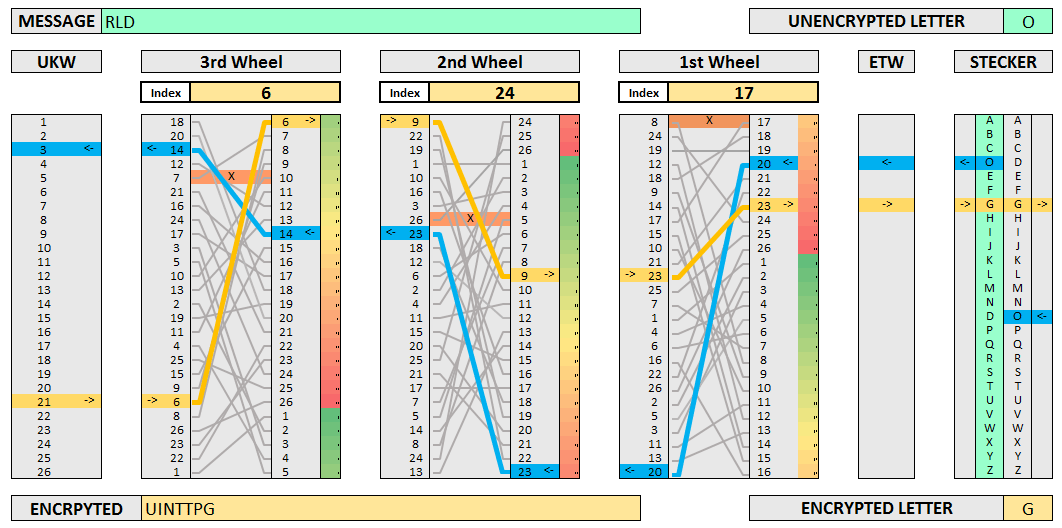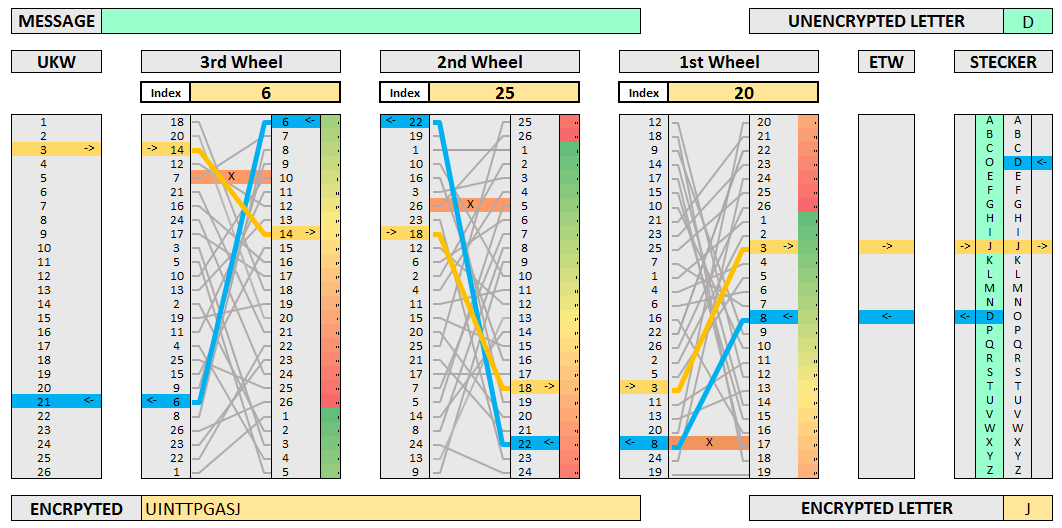



Learning The Enigma With Recurrent Neural Networks




Enigma Machine Wall Street International Magazine



The Polish Attack On Enimga




Enigma Machine Simulator Program About Code Name Verity Spies Etc Enigma Aspectos Historia
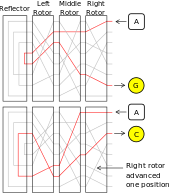



Enigma Machine Wikipedia




Enigma Machine Images Stock Photos Vectors Shutterstock




Cryptanalysis Of The Enigma Wikipedia




The Enigma 1




How Did The Enigma Machine Work Computing The Guardian



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Pin On Cryptography




Ultra Allied Intelligence Project Britannica




Enigma Machines Build Complex Codes But Can T Even Add Two To Two Cnet




Enigma Machine Goes On Display At The Alan Turing Institute The Alan Turing Institute




Enigma Machine Brilliant Math Science Wiki




Enigma Definition Machine History Alan Turing Facts Britannica



c History Enigma Pictures Video Facts News



Gc1vz Darwin Enigma Challenge Unknown Cache In Northern Territory Australia Created By Gibbo003



Teaching History With 100 Objects Enigma Cipher Machine
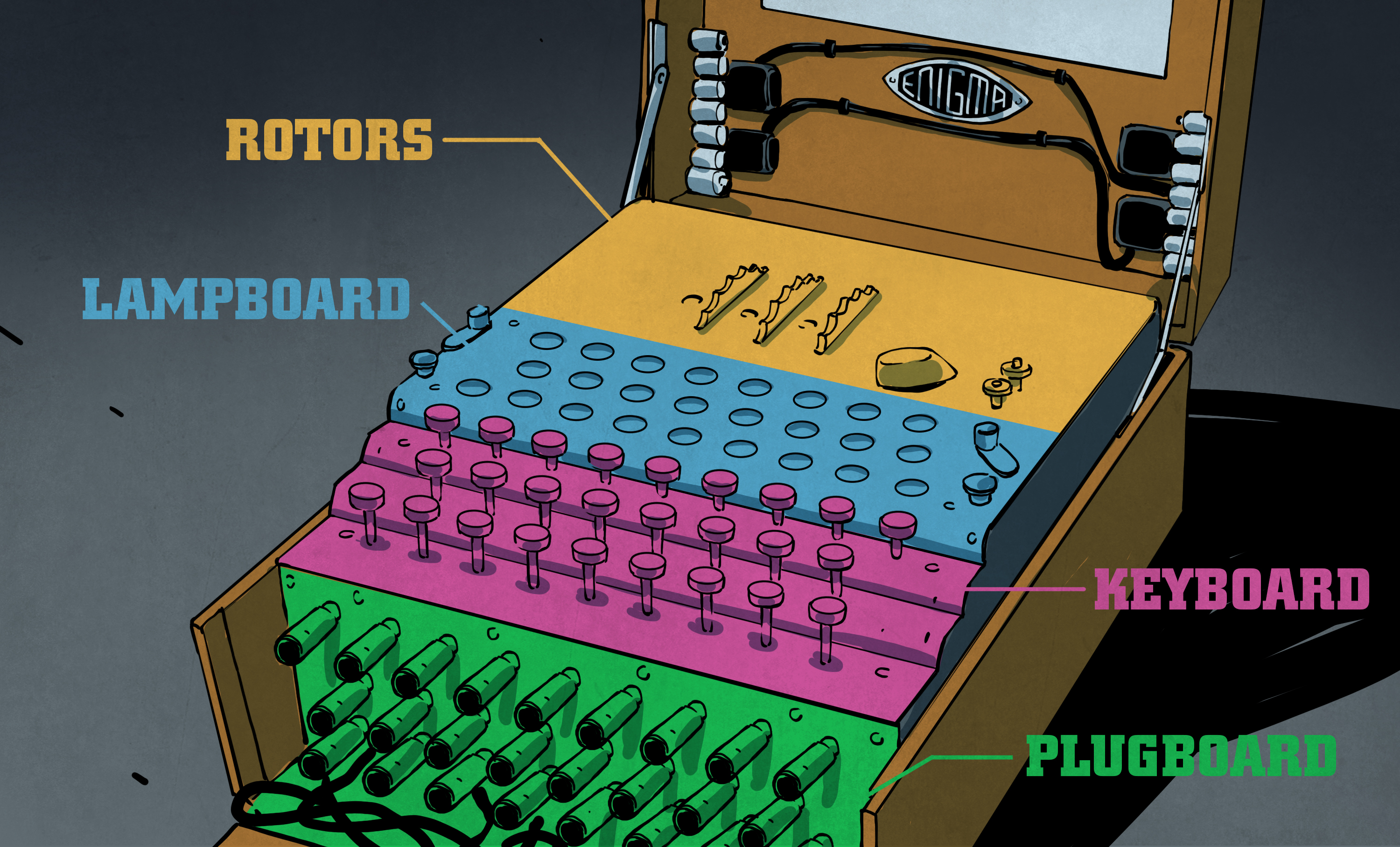



The Enigma Enigma How The Enigma Machine Worked Hackaday



What Is The Enigma Cipher Machine



0 件のコメント:
コメントを投稿